If you are an employee at ESU, you may have received an email from our Payroll department this week warning you of a new IRS email scam.
The IRS released a statement on November 19 warning the public of fraudulent emails impersonating the IRS. While similar scams have been used in the past to impersonate banks and other financial institutions, this particular email pretends to come from "IRS Online" and includes a malicious attachment called "Tax Account Transcript." The attachment carries a well-known malware and has a great potential to infect your computer.
It is extremely important that you do not open this email or its attachment. The IRS (or any other legitimate institution) will never send unsolicited emails to the public containing sensitive information, such as tax transcript. If you receive an email like that in one of your personal email accounts, you can delete or forward the scam to phishing@irs.gov.
If you receive this scam to your ESU email, please contact the IT Help Desk immediately at ext. 5555.
In honor of National Computer Security Day, follow our basic computer security tips found here!
Friday, November 30, 2018
National Computer Security Day!
 November 30th is National Computer Security Day! Computer security is a vital step in protecting your accounts and information since your computer is typically your storage spot for everything. This is largely due to the fact that it's convenient and comfortable to you. Sometimes it being too comfortable leads to us not taking proper steps to ensure everything is secure. Therefore, the following are some quick tips on how you can secure your computer:
November 30th is National Computer Security Day! Computer security is a vital step in protecting your accounts and information since your computer is typically your storage spot for everything. This is largely due to the fact that it's convenient and comfortable to you. Sometimes it being too comfortable leads to us not taking proper steps to ensure everything is secure. Therefore, the following are some quick tips on how you can secure your computer:Have Antivirus Software
Start with running a scan for any form of spyware or malware. This will provide a fast and efficient way to make sure your device doesn't already have some form of malicious software harming it. If you don't have any installed and are a student or staff/faculty at Emporia State University, you can get a free copy of this software. To do so, simply go the help desk website and follow through downloading/set up.Always Update
Next check to see if all of your applications and software's are updated. It's best to do this often, especially with apps, because of the constant updates being provided to you. This will allow you to find/schedule a time for your updates to complete on a regular basis. If they aren't updated, be sure to do this because updates tend to include better security or fixes to bugs. Overall, by updating your protecting and providing a better service to yourself.Check Downloads
Finally, always check before completing a download. One way hackers target people is by inserting malicious software or viruses into downloads. These can be through emails, apps, or websites; therefore, new just assume because it's available to you it's safe. Always take a second to see who is providing the download to you and any suspicious signs. These signs could include misspellings, executable files (.exe, .bat, etc.), and the size of the download (too small or too big for what it should be).
Learn more by visiting hornet.emporia.edu and clicking on the "Information Security" tile. Finish the semester strong!
Learn more by visiting hornet.emporia.edu and clicking on the "Information Security" tile. Finish the semester strong!
Monday, November 19, 2018
Cyber Shopping Tips!
 With the holidays approaching fast it's important that we take the time to refresh our cyber skills. This is especially true with Black Friday and Cyber Monday being only a few days away. Each of these "holidays" are about taking advantage of great deals, but we need to make sure hackers aren't taking advantage of us while shopping. Here are a few quick tips for protecting your information while protecting your back account during this shopping season.
With the holidays approaching fast it's important that we take the time to refresh our cyber skills. This is especially true with Black Friday and Cyber Monday being only a few days away. Each of these "holidays" are about taking advantage of great deals, but we need to make sure hackers aren't taking advantage of us while shopping. Here are a few quick tips for protecting your information while protecting your back account during this shopping season.Check the Website
During this busy shopping season, it's important to check what sites your getting your deals on. Chances are you're clicking the sites with the best deals, but those might not be the safest ones to use. Always make sure you evaluate the reviews to make sure its a legitimate and safe site. One great source for authenticity is the Better-Business-Bureau. It will provide a rating and relevant reviews of the business.Look for Https
One key step in making sure your information is safe when processing a payment is looking for https rather than http. Another way to check the security of a website is to look at the lock symbol to the left of your web address. If it is closed it is a secure site, if not be cautious about the information you put into the site. Since https is used when a site in secured and uses encryption to protect data, it is a protected site.Watch for Scams
Recently there has been news about a new form of phishing popular during the shopping season. This involves emails that appear to come from popular online shopping sites, like Amazon. They state that there has been an issue with your order and instructs you to click a provided link. This link takes you to a site designed to collect your information and then store it for the hackers use. Therefore, if you do have orders for that site go directly to the site to check the status of your orders.Secure your Information
Finally, make sure your are taking steps to protect your information. This can be done through keeping complex passwords unique to each account. Make sure you don't save your login information to any device, since this can open your account to unwanted individuals. If possible limit what sites have access to your financial information, as this can protect you in cases of a breach. Simple checks and securities now can keep you from major issues later on.Friday, November 16, 2018
Eerie or Revolutionary? You Decide.
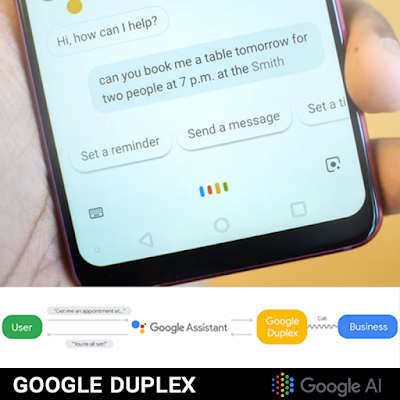
Google announced Google Duplex during the Google I/O 2018. This is a new revolutionary technology that allows your AI personal assistant to conduct natural conversations and carry out “real world” tasks over the phone.
Imagine telling your Google Assistant to complete tasks such as scheduling hair salon appointments, or even booking a table at a restaurant. The system is very well developed and conversations between a fully automatic computer system and real businesses sound natural and human like. This is a huge leap in Artificial Intelligence technology as the assistant can understand complex sentences, fast speech, and long remarks, so it can respond naturally in a phone conversation
It will positively impact businesses who regularly schedule clients like doctors and lawyers and could have the A.I. do that on their behalf. Small businesses can also benefit, as research shows that 60 percent of small businesses who rely on customer bookings don’t have an online booking system, according to Google’s blog.
Final release dates are yet to be announced, and is most likely to arrive first in the Google Pixel phones.
For more information see what Google has to say; eerie or revolutionary? You Decide.
Saandhyarag Sasidhar
Student Operations Manager
Web and Digital Strategies
Do More With Your Wix Sites
 Whether a student is a Web Designer, looking to make a personal website, or already has a website, students can customize more with "Wix Code" implemented by Wix.
Whether a student is a Web Designer, looking to make a personal website, or already has a website, students can customize more with "Wix Code" implemented by Wix.Wix created Wix Code which is an Integrated Development Environment (IDE) similar to Atom.io, NetBeans, Microsoft Visual Studio, and many other IDEs that allow a user to develop a website how they want/need. The code/programming languages Wix Code uses are HTML (site structure), CSS (site aesthetics), and JavaScript (site behaviors).
Building on website with Wix now gives users four major categories for building sites: Front End, Back End, Database, and additional components.
Wix provides students with a great option for building personal websites and is used by ESU for a number of special project sites and communication needs.
Donald Goode
Student Web Developer
Web & Digital Strategies
Wednesday, November 14, 2018
Careers in Cyber-Security!
 This week is National Cyber-security Career Awareness Week! Chances are you've never really considered a career in cyber-security since its a relatively new area. While many careers are clearly outlined and expected we're in a time of frequent data breaches, cyber-security is a continuously growing and evolving career field. This means that the amount of open positions and the demand for qualified applicants is incredibly large. So, its a great time to consider stepping into the cyber-security area.
This week is National Cyber-security Career Awareness Week! Chances are you've never really considered a career in cyber-security since its a relatively new area. While many careers are clearly outlined and expected we're in a time of frequent data breaches, cyber-security is a continuously growing and evolving career field. This means that the amount of open positions and the demand for qualified applicants is incredibly large. So, its a great time to consider stepping into the cyber-security area.Characteristics
What make you suited for a job in cyber-security? People who normally want to problem solve through thinking critically typically excel in the area. Now while you make think the issues are purely technical, this isn't true. The issues can be in anything from behavioral, legal, logistical, technical, and financial. All of these areas must be considered when analyzing cyber-security because all of them pay an integral part in the overall position. For example, you might think that behavior has nothing to do with cyber-security; however, you must take into account how users and hackers will use your programs with different intentions.Benefits
One great thing about careers in cyber-security is the fact that they are constantly being added to make up for the growing need. They are also still developing a lot of the positions, which means that were is a level of excitement and unpredictability. It's not your typical office position where you'll have repeats of the same mundane day, there's always something going on somewhere in the world affecting you. Examples of this could be new technologies, changes in policies, or even breaches.Requirements
Now that that you're interested in the area, its important to know what you'll need to get into this field. The majority of these positions will ask for a bachelors degree with a major in cyber-security, information technology, or computer science. From there, it's recommended to complete some form of advanced training, typically a masters program or security clearances. However, some employers may only need a certificate to consider you for the position. To make sure you're on the right track look up potential companies you might be interested in and see what they require.Friday, November 9, 2018
How Clean is Your Machine?
Many of us get caught up in our everyday tasks that we forget to take a second to make sure our devices are clean. Now I don't mean clean as brushing off the dust (which is still a good idea). Keeping a clean machine means updated, protected, and cleaned.
Update
While it seems like there is always so form of update coming out, they really do serve an important purpose. A lot of update include fixes for security issues or a new form of security. By not updating your devices you could be putting yourself in harms way. So, whether it's your phone, tablet, or computer take that minute to keep your software up to date.Protect
Always keep your passwords secure and unique. Chances are the password you've been using since freshman year of high school isn't as safe as it could be. Changing it to a pass phrase that includes special characters, numbers, and capitalization can be a great first step to protecting your accounts. Next, implement 2-factor authentication for your accounts. This will require you to prove that you're you, but it means that someone who isn't you can't access your information.
Clean
Finally go through your old documents or applications and get rid of what you don't use. A lot of apps require certain permissions that might not be relevant to the true purpose of the app. For example, a calculator app probably doesn't need access to your pictures or contacts. By clearing out unnecessary applications your taking one step further in securing your accounts and cleaning your machine.
Thursday, November 8, 2018
myIT Tip of the Week
Banner 9 is Live!
Are you an INB user? Banner 9 Administrative Pages are now live and will soon take the place of INB. The current (INB) Banner 8 will be shut down on December 3, 2018.
You can find links to Banner 9 under Quick Links in BuzzIn or go to hornet.emporia.edu, click on ‘Faculty’ or ‘Employees’ and then click ‘Go’ on the Banner 9 tile.
Currently, INB takes a separate password, with Banner 9 you will no longer need a separate password, just log in with your ESU username and password. Running Banner 9 is no longer dependent on using Java, which means you are no longer limited to using Internet Explorer. You may use any browser to access it. Google Chrome is the recommended browser.
Right now, you can use INB or Banner 9. We recommend that you begin using Banner 9 to familiarize yourself with the new interface. Both INB and Banner 9 are running in parallel. So, any changes you make in one system will carry over to the other.
The SSB portion of Banner will not be upgraded to Banner 9 at this time. You will continue to access SSB through the links in BuzzIn.
Friday, November 2, 2018
Check-ups are for More Than Just Colds
 When was the last time you had a check up? You've probably had a medical check up within the few months for something minor. Chances are when you read check up you assumed that's what I meant. But, when was the last time you did a security or privacy check up on social media? Check-ups are an important way to make sure everything is working properly and actions don't need to be taken, both physically and virtually. Facebook in particular has a great check-up system in place to make sure your settings are what you are comfortable with. There are 3 areas in particular to be careful with on Facebook that the check up covers.
When was the last time you had a check up? You've probably had a medical check up within the few months for something minor. Chances are when you read check up you assumed that's what I meant. But, when was the last time you did a security or privacy check up on social media? Check-ups are an important way to make sure everything is working properly and actions don't need to be taken, both physically and virtually. Facebook in particular has a great check-up system in place to make sure your settings are what you are comfortable with. There are 3 areas in particular to be careful with on Facebook that the check up covers.The first area is your privacy. This covers who can see your future posts and your previous posts. Knowing who has access to what you have on your account is vital. What you might show to your best friend is probably different from what you would show your coworkers or future employer.
The next area is your photos. Not every picture taken should be posted to everyone on social media. An easy way to limit who has access is to change your audience. This could be making it so only your friends or custom groups can see those unflattering pictures.
The third area is your profile. Depending on how you have your account set up, you could have a lot of information on your profile. Overall, what do you want the public and your friends seeing. This can also go a step farther with who can look you up or contact you on Facebook. Always make sure that you are comfortable with who it's available for.
Take the Facebook privacy check-up by clicking here!
Subscribe to:
Posts (Atom)